In this, We will integrate the NSX-T Manager with our Active Directory (AD) so We can use the Domain Account to log in instead of default admin. In an upcoming post, We will discuss how to integrate NSX-T with VMware Workspace One Access (Formerly known as VMware Identity Manager (vIDM) as well. Workspace One Access is VMware’s Identity Provider to the majority of their products.
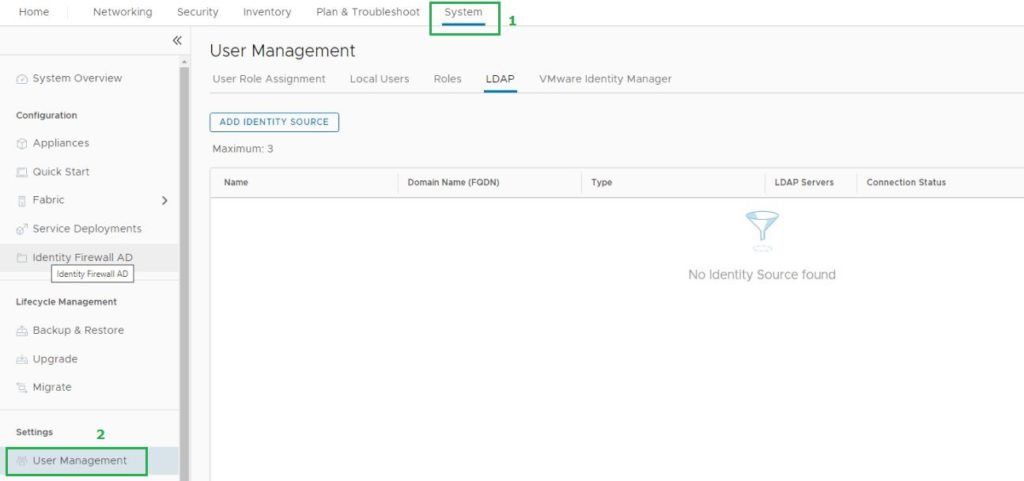
System – Settings – User Management – LDAP
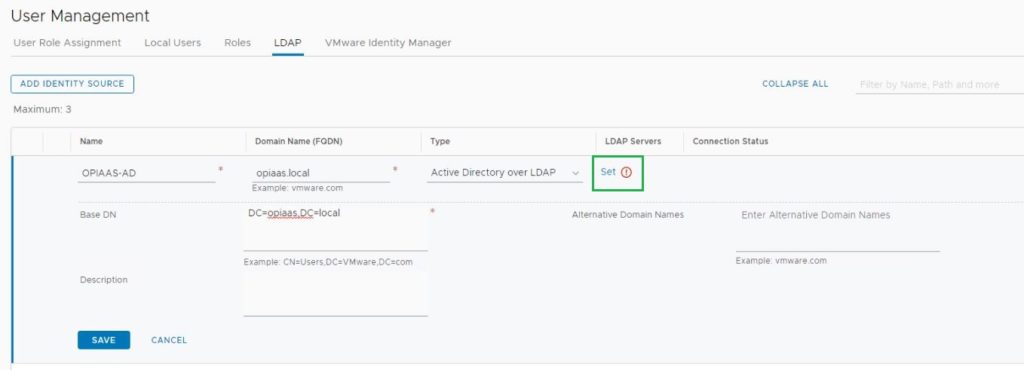
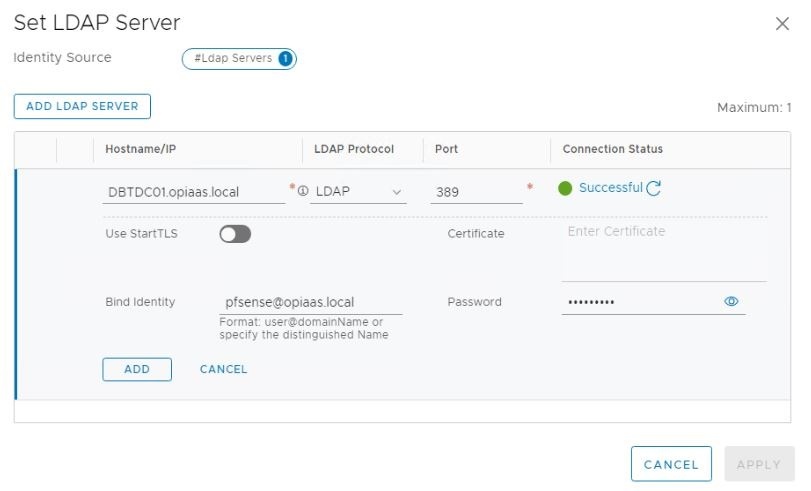
I’m using LDAP instead of Secure LDAP since I don’t have a Trusted CA SSL Certificate for my NSX-T Manager (Still using the Sel-Signed Certificate). If you have an SSL certificate installed from your Internal CA you can use the Secure LDAP (TCP 636) option.
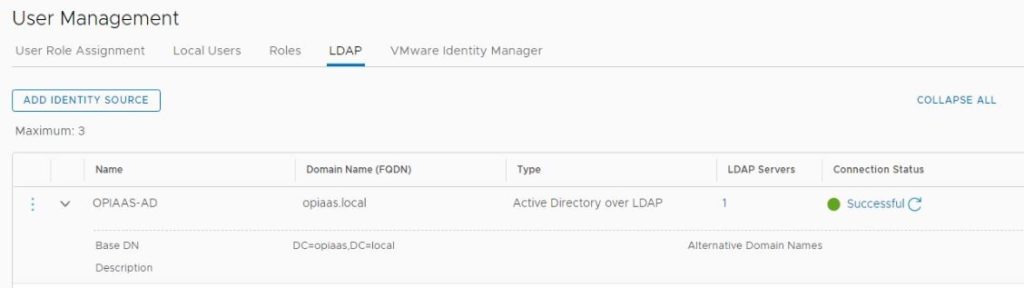
Now we have integrated the NSX-T Manager with AD, I will add my domain user name to NSX-T Enterprise Admin Group. Before that let’s discuss built-in Roles in NSX-T Manager. NSX Intelligence recognizes the following built-in roles.
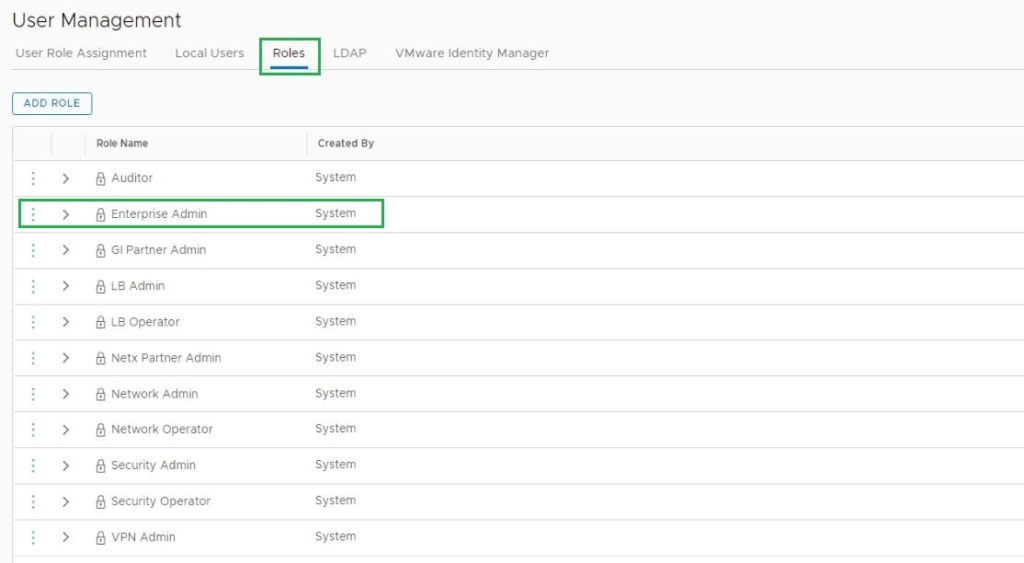
For more information regarding NSX-T RBAC, Refer to the link from VMware
Role-Based Access Control in NSX Intelligence
To add the Users/Groups, Go to the User Management.
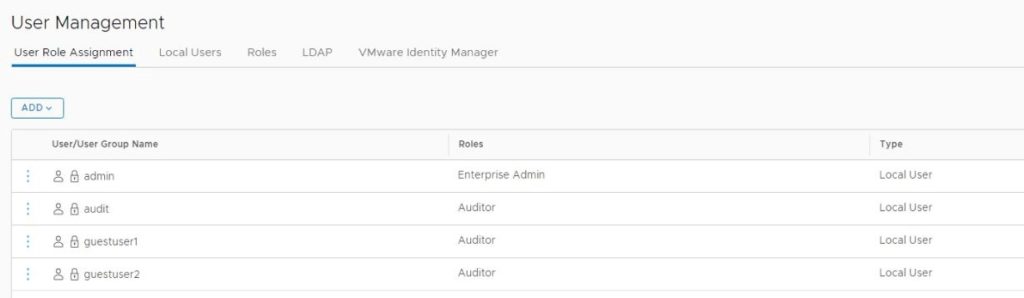
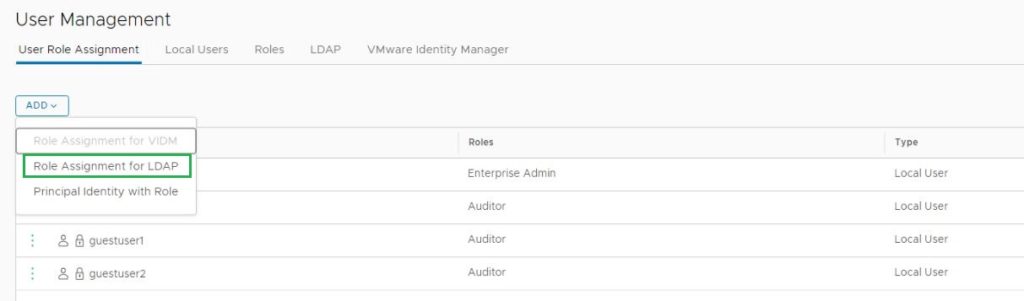
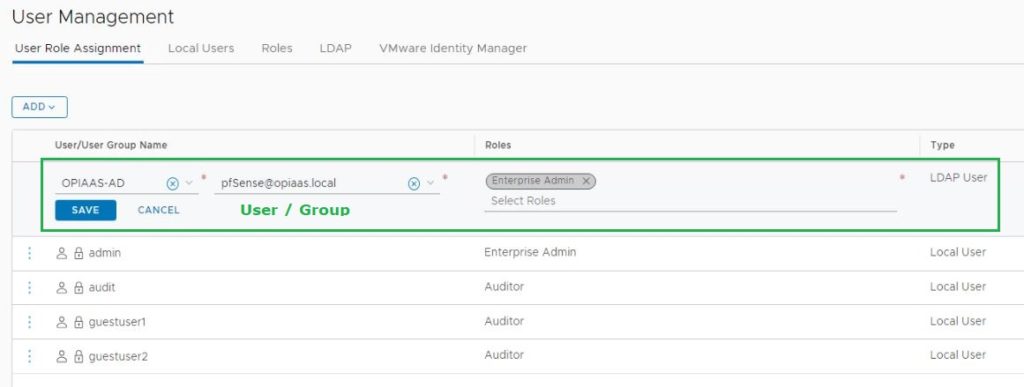
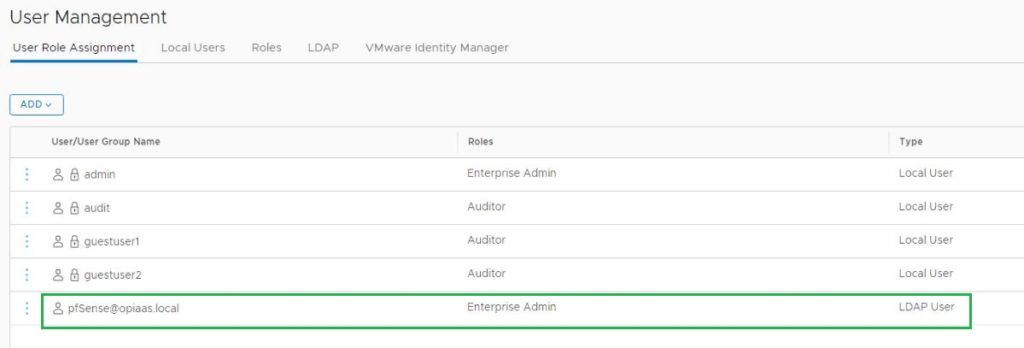
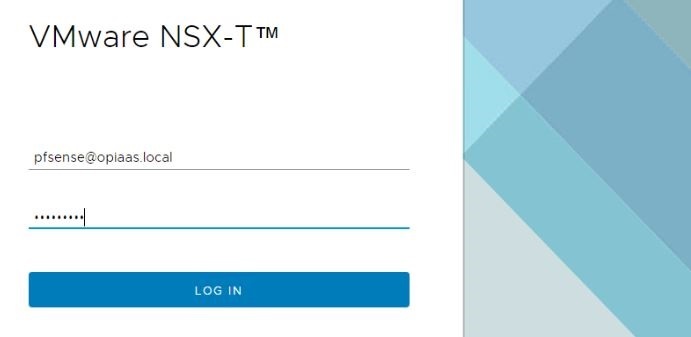
* Screenshots captured from VMware vCenter Console and NSX-T Manager Console on Feb 02, 2022.